This domain (www.cognifyhub.net) is for sale. for inquiries, please email inquiry@ginoborlado.org
Fake AI Tools Infect Windows and macOS Devices with Stealthy Malware
Learn how fake AI tools are spreading malware disguised as legitimate software. Discover how cybercriminals use fake image and video generators to infect Windows and macOS devices, stealing passwords, cryptocurrency wallets, and sensitive data. Find out how to protect yourself from these evolving threats.
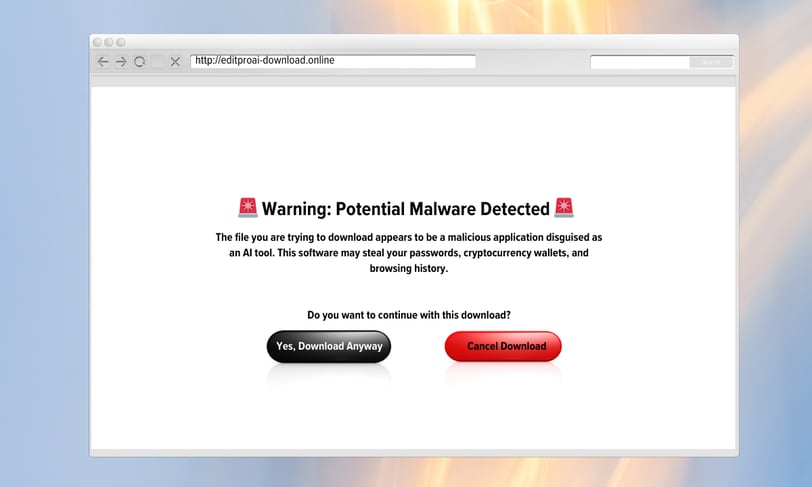
The surge in popularity of AI tools has opened up new opportunities—not just for users, but also for cybercriminals. Recently, fake AI image and video generators have been spreading malicious software that targets both Windows and macOS systems. The aim? To steal sensitive information like passwords, cryptocurrency wallets, and browsing data.
The Deceptive Tactics of Fake AI Tools
Cybercriminals have become clever in their approach, setting up fake websites that imitate legitimate AI applications, like the supposed “EditProAI.” These sites are designed to look professional, complete with cookie consent banners, making them appear credible. They are promoted through search ads and posts on social media platforms like X (formerly Twitter), where they lure users in with viral deepfake videos.
Once a user clicks the download link, they receive what looks like a genuine software installer. For Windows, it’s disguised as “Edit-ProAI-Setup-newest_release.exe,” and for macOS, it’s “EditProAi_v.4.36.dmg.” However, these files hide dangerous malware ready to exploit the victim’s device.
The Two Malware Variants: Lumma Stealer and AMOS
The fake AI tools deploy two main types of malware:
Lumma Stealer: Targets Windows devices, aiming to steal a wide range of sensitive data. It focuses on harvesting credentials, stored cookies, cryptocurrency wallet information, and credit card details from web browsers like Chrome, Edge, and Firefox.
AMOS: Designed for macOS, AMOS behaves similarly, collecting data from various apps and browsers. It targets stored passwords and other personal information, making it a serious threat to users of Apple devices.
Both malware variants send the stolen data back to a command-and-control server, where attackers can either use the information for further attacks or sell it on dark web marketplaces.
How the Attack Unfolds
The attack begins with users encountering ads or social media posts promoting deepfake videos. Clicking on these links directs them to fake websites mimicking the EditProAI software. These sites look polished and include common design elements like cookie consent pop-ups, which build trust and lower users' suspicions.
Once on the site, users are prompted to download the software. The Windows version of the malware even uses a stolen code signing certificate, making it appear legitimate. After installation, the malware operates quietly, collecting data like passwords, cryptocurrency wallet keys, and browsing history. The collected data is then sent to the attackers’ server for future use or sale.
What’s at Risk: The Scope of Data Theft
The impact of this malware is significant. Once infected, users face the risk of losing:
Saved Passwords: Stored credentials for email, banking, and other online services.
Cryptocurrency Wallets: Keys and wallet data, which can result in the theft of digital assets.
Credit Card Information: Payment details saved in browsers or apps.
Browsing History and Cookies: Information that can be used to impersonate the victim or conduct further attacks.
This stolen data is valuable on the dark web, where cybercriminals sell it or use it for phishing campaigns, data breaches, and financial fraud.
How to Protect Yourself from These Fake AI Tools
If you suspect that you may have downloaded one of these malicious programs, take immediate action:
Reset All Passwords: Change your passwords for all accounts, starting with the most sensitive ones like banking and email.
Enable Multi-Factor Authentication (MFA): Adding an extra layer of security can help protect your accounts even if passwords are compromised.
Be Cautious with Downloads: Always verify the source of software, especially when it’s promoted through ads or social media.
It’s also a good idea to regularly monitor your accounts for unusual activity and consider using a reputable antivirus program to detect and remove potential threats.
The Growing Threat of Infostealers
Information-stealing malware, or infostealers, have seen a sharp rise in recent years. Attackers are constantly finding new ways to distribute these malicious tools, from exploiting zero-day vulnerabilities to sharing fake fixes on forums like GitHub. This trend underscores the need for heightened vigilance and better security practices among users.
Cyberattacks involving infostealers can lead to severe consequences, including data breaches, financial loss, and even identity theft. As we saw in recent high-profile breaches, compromised credentials can disrupt corporate networks and cause extensive damage.
Conclusion: Stay Alert and Informed
The spread of fake AI tools like EditProAI is a reminder of how quickly cyber threats can evolve. While the technology behind AI is exciting, it’s crucial to approach new tools with caution. Users should stay informed, verify software sources, and take proactive steps to protect their data.
